The narrow-band speech concealment technology proposed in the communication system designed in the solution overcomes the large amount of conventional cover speech media and is not suitable for narrow-band transmission, especially the transmission of such format speech on the network is easily suspected by attackers. The hidden algorithm based on low bit stream cover speech (G.729) makes the application environment of the hidden system more extensive.
0 Preface
With the development of network technology and information technology, network information security issues have become increasingly prominent. The openness of the IP network brings convenience to people, and it also leaves a security risk to the information transmitted by the network. Hostile forces can easily conduct wiretapping, network capture, counterfeiting, and tampering, posing a serious threat to the secret information transmitted over the network. The traditional means of information security is to use cryptography to implement various transformations in plaintext so that it is not understood by outsiders. However, this means of encryption also exposes the existence of secret message transmission while protecting secret information, which is likely to attract the attention of attackers. Even if the attacker cannot decipher the password, the attacker can tamper with, replace, or send a fake message to destroy the transmission of the information.
Under the conditions of modern information warfare, the security and confidentiality of traditional communication methods are bound to undergo profound changes, so as to resist the enemy's information attack, improve the anti-interception and anti-interference ability in the confrontation, and ensure the safe transmission of data. In order to effectively combat various attacks, especially the military, new methods of data security and confidential communication must be studied. Information hiding technology is an important research direction that has emerged to solve such problems. The emergence of information hiding technology has effectively improved information security. The use of images, video, audio and other media as a cover carrier for secure transmission of secret information is a common method for information hiding. At present, most of them are civil or military networks, and most of them are based on IP networks. The voice communication between people is gradually shifting from traditional telephone to VoIP. Nowadays, both individuals and enterprises are more and more like to use IP phones, network chat and other means of communication, such as voice through VoIP, SKYPE, MSN or QQ. Communication.
Such speech is a high-compression, low-bitrate signal. Concealed communication with the most commonly used compressed speech number as a cover carrier can reduce the suspicion of the attacker, but the compression signal brings difficulty to the hidden. In this paper, the G.729 compressed speech stream information hiding algorithm based on low bit rate is studied, and the IP network voice concealed communication system is designed.
Information hiding technology based on audio signals has been widely studied by scholars at home and abroad, and it mainly focuses on embedding secret information on audio formats such as WAV and MP3. A covert communication algorithm for concealing secret information in a compressed voice stream of a GSM network has been proposed. It has also been proposed to transmit a watermark embedded G.729 voice stream in a PSTN network, and proposes an application idea of ​​transferring the described scheme to an IP network. Some people have given a covert communication mechanism based on streaming media. In this paper, a new IP-based compressed voice covert communication system solution is proposed by means of information hiding. It meets the requirements of IP network for secure communication transmission technology, and the transmission characteristics of IP network are designed accordingly. Better adapt to the transmission environment in IP networks. The system can operate on the Internet, military information networks, and future military field networks, greatly improving the security and concealment of data communications.
1 Technical principles and implementation
Echo on the IP network uses high-efficiency compression algorithms, such as G.711, G.723, G.726, G.729, etc. The voice stream rate is too high, and the network bandwidth requirements are too high. Therefore, the compressed speech with low bit rate is often used. flow. The system selects the 8 Kb/s G.729 speech compression algorithm to compress the carrier speech and embed the secret information in the compressed data stream. The dense voice stream maintains a constant rate of 8 Kb/s, which makes the system not only run on high-speed LAN, Internet and military information networks, but also on low- and medium-speed IP networks, such as mobile wireless data networks, military field networks, etc. surroundings.
1.1 G.729 speech compression algorithm
G.729 is an 8 Kb/s speech coding scheme published by ITU.T in 1996. It uses various advanced technologies of speech compression coding to achieve long-distance telephone sound quality and has been widely used in personal communication and satellite systems. . Sampled by 8 kHz, quantized into a 16 b linear PCM digital signal input to the encoder. The encoder is based on a linear predictive analysis synthesis technique to encode the energy of the auditory weighted differential signal between the actual speech and the synthesized speech as much as possible.
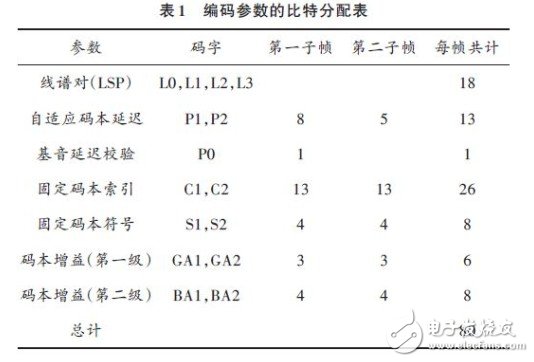
The encoder (see Figure 1) processes a 10 ms long speech frame, each frame divided into two sub-frames. A linear prediction (LP) analysis is performed every frame, and the LPC parameters are converted to a line spectrum, and the predicted two-stage vector quantization (VQ) is performed on the LSP form. The analytical parameters are then used to extract the excitation parameters. The excitation parameters (including fixed codebook and adaptive codebook parameters) are calculated once per subframe (5 ms). Each frame is subjected to an open-loop integer base pitch delay estimation using perceptual weighted speech, and then a closed-loop fractional pitch analysis is performed to determine the delay and gain of the adaptive codebook, and a fixed codebook search is performed below. The gain of the adaptive codebook and the fixed codebook is vector quantized using a predictive two-stage conjugate structure codebook. Refer to the G.729 audio standard ITU RecommendaTIon G.729, and obtain the bit allocation of the coding parameters as shown in Table 1.
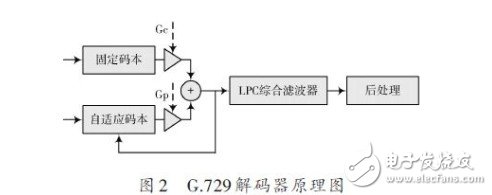
At the G.729 decoder end (see Figure 2), the LSP coefficients and two fractional pitch delays, two fixed codebook vectors, and two sets of adaptive codebooks and fixed codebooks are extracted from the received codestream. Gain and other parameters. The LSP parameters are then interpolated and converted to the form of linear prediction filter coefficients. Next, the adaptive codebook and the fixed codebook vector are multiplied by respective gains and then added to obtain an excitation signal. After the excitation signal passes through the LPC synthesis filter, a synthesized speech signal is obtained. Finally, the synthesized speech signal is post-processed to improve the quality of the synthesized speech.
Kitchen series are linear actuators that can be used in kitchenware to make it smart. With actuators, extractor hood can be hide, working cabinet can be adjustable to the suitable height, and wall cabinet can be up and down, etc. Some are tiny enough for limited space, some are long and strong enough (15,000N) for big load.
Kitchen Actuator,Kitchen Ventilator Actuator,Kitchen Linear Actuator,12V Kitchen Actuator
TOMUU (DONGGUAN) ACTUATOR TECHNOLOGY CO., LTD. , http://www.tomuu.com