With the increasing mobility of people, new demands for the security and reliability of identity authentication have emerged, pushing virtual authentication to replace key card access control. In order to cope with the challenges of uninterrupted connectivity and the explosive growth of fully distributed smart devices, it is necessary to develop an infrastructure solution to support evolving access control system applications and to drive all related new product development efforts. Near Field CommunicaTIoNS (NFC) is a technology that is expected to achieve the above objectives, but to ensure its security, the industry must establish an integrated chain of custody-based authentication method - by this method, the system Or all endpoints in the network can be authenticated so that authentication information between endpoints can be reliably transmitted at all times.
1 System Introduction
TIP is a secure and trusted network that provides an authentication transport framework for the delivery of secure products and services. It is a comprehensive framework for creating, delivering, and managing secure authentication. Simply put, the infrastructure is a central security repository that is based on a secure network connection and is based on a publicly available encryption key management security policy. For known endpoints (such as credential cards, card readers, what is a card reader?
As the name implies, a card reader is a device that reads a memory card. Memory cards are now available in a wide range of applications, from digital cameras to MP3 players, from PDAs to more popular multimedia phones. Currently, the most common memory cards on the market are SmartMedia (SM card), CompactFlash (CF card), MemorySTIck (Sony Memory Stick), MulTIMediaCard (MMC card), SD Memory (SD card), IBM Microdrive (IBM Microdrive). And the latest XD-Picture (XD card). And printer) service delivery. HID Global refers to it as a “regulated†system—all devices connected to the system are known to exchange information reliably and securely. The TIP architecture is fully scalable, and its transport protocols and encryption modes conform to a variety of standards to support multiple applications. TIP systems can also implement virtualization and cloud-based models to deliver service delivery over the Internet without compromising security.
TIP provides a protected authentication transport network that verifies all endpoints or nodes in the network, so the information transfer between nodes is trusted.
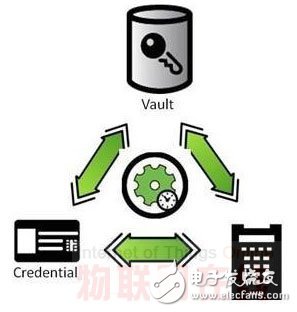
TIP model diagram
The TIP model (shown above) contains three core elements, the Secure Vault, the Secure Messaging method, and the Key Management Policy and Practices. The security library provides secure key storage for known and trusted endpoints. The secure communication method uses a symmetric key method that conforms to industry standards to transmit information to each endpoint. The key management policy and specification set the security repository. Access rules and rules for distributing keys to endpoints.
2 How to establish endpoints and reliable information transmission
Only after the TIP node protocol is implemented will the endpoint be enabled and then recognized by the "secure library" and registered as a reliable network member. The endpoint then communicates with the Security Library.
Endpoints such as credential cards, card readers, and printers communicate with the "safety library" through software workflows, and their access and processing rules are strictly controlled by HID Global's "key management policies and specifications" - only certified devices It is possible to join the network (unlike any Internet where any computer can access any website), thus forming a hidden and strict authentication mechanism.
TIP messages between endpoints are encrypted using industry-standard encryption methods for secure information transmission in compliance with public security policies. These TIP information packets are protected by two nested symmetric keys, which contain "Secure Identity Object" (SIO) information. Multiple SIOs can be nested into a single TIP message to provide a variety of instructions to a variety of different devices, such as access cards, smartphones, and computers. Each device can have different access control features if necessary. For example, the simplest SIO is to simulate the credential program data on an iCLASS card.
Once the authentication between the "secure library" and the endpoint device is passed, the device is considered "trusted" in the network. Trusted devices no longer need to communicate with the secure library and can work independently. In this way, the transmission of information between endpoints (such as credential cards and card readers) is "trusted", and the resulting transmission of information (such as opening a door or logging into a computer) is also considered To be "trustworthy."
With the support of short-range wireless communication technology, mobile phones using this technology can be supported as TIP endpoints, so they can be programmed with different SIOs to implement analog cards or more complex applications, not only authorized to pass RFID. The /xinpin/menjinkaoqin/'target='_blank'" access control system can also implement complex access control rules that are interpreted by itself.
3 Development status and prospects
TIP has been deployed since the end of 2010 and has announced its partnership with HID Global's first partner, NCF chip leader INSIDE CONtactless, to take the lead in a believable, virtual and on-demand authentication network. step. INSIDE Contactless is one of the few companies that are driving NFC trials around the world. This groundbreaking collaboration will enable NFC-enabled handsets to incorporate iCLASS access control and credential information like physical smart cards. This credential information will be provided through HID Global's TIP system and will be used in conjunction with other network services and real-time communications in the future. HID Global plans to launch other similar partnerships that combine HID Global's non-contact solutions with other vendors, NFC technology and other widely used technologies for user authentication, cashless vending and computer security. Sign in and other applications to create a platform that is widely available (covering everything from mobile phones to laptops). These platforms and applications will significantly increase the value proposition of contactless smart card credentials.
At Christmas it is nice, in addition to the tree decorated with
large and colorful Christmas balls, to surround yourself with
decorations with Christmas motifs to be distributed around the house.
Create the right atmosphere with this led light garland.
Portable & Versatile
1.The item have a base and could stand on anywhere.
2.Integrated hanging hook holes for ease of display on wall or just rest on mantle, self, table or dresser.
3.Can be displayed standalone or combined with other pieces to create an eclectic lighting installation.
3.Create a whimsy showpiece on the cake or candy table during the Wedding.
Christmas Motif Lights,Led Motif Light,Christmas Motif Led Rope Light,Christmas Motif Light Decoration
XINGYONG XMAS OPTICAL (DONGGUAN ) CO., LTD , https://www.xingyongxmas.com