With the rapid development of the Internet of Vehicles, the application of the vehicle terminal has become more and more extensive, and the exposure to various information security threats has been increased, forming a security requirement for the functional characteristics of the vehicle terminal. The author analyzes various information security threats faced by vehicle-mounted terminals from various angles, summarizes information security requirements, and proposes corresponding technical measures.
This article refers to the address: http://
1. The business function of the vehicle terminal and the corresponding information security requirements
The emergence and popularity of in-vehicle terminals is a more convenient and pleasing experience for drivers and passengers, so the functions are also very rich and growing. The current vehicle terminal mainly includes the following functions:
(1) Basic vehicle condition collection display
This type of function started earlier, and the early vehicle status information includes parameters such as tire pressure, fuel quantity, tank temperature and outside temperature, which are displayed in the traditional instrument panel. Emerging electric vehicles also display electricity information. When the intelligent vehicle terminal is widely used, the information is displayed on the display screen of the vehicle terminal, and the user has a unified control interface to enhance the user experience.
(2) Remote operation
These include remote unlocking, remotely launching vehicles, and remotely turning on air conditioners. These applications are usually combined with the network, and the user operates the vehicle remotely through the mobile phone APP or the web page providing the corresponding service, which greatly improves the convenience.
(3) Help and remote rescue
The same is done through the network. At present, a large number of vehicles have built-in T-Box system, the system integrates SIM card, can connect to the operator network, upload the state system stored in each ECU of the vehicle to the TSP platform for maintenance personnel to refer to the diagnosis. Many T-Box provides a one-button rescue service, and the system automatically completes multiple tasks including diagnosis and positioning of vehicles, improving the efficiency of handling urgent problems.
(4) Navigation
It is the main function of the car Infotainment system. In actual use, the navigation app connects to the network to get real-time traffic information. The way to connect to the network can use the Wi-Fi hotspot provided by the vehicle user's mobile phone, or directly access the cellular network through the built-in SIM card.
(5) In-car entertainment
Such applications have gradually become networked, and the popularity of downloading, online viewing, and the like has brought a better user experience to vehicle users. In order to improve the clarity and fluency of the video, the image processing capability of the vehicle terminal hardware is also gradually improved.
(6) Self-driving
Autopilot is a popular application. Starting from automatic parking, the driver's control of the car is reduced, driving becomes easier and more relaxed. At present, auto-driving cars have been tested by actual roads, but this technology requires a certain amount of time to officially commercialize on a large scale.
In the process of automatic driving, the vehicle collects a large amount of road information, and the position information of people and objects around the vehicle body is calculated according to the information such as the speed direction of the vehicle and the traffic management regulations, which requires the vehicle terminal to have sufficient computing power and real-time performance. . With the development of vehicle-vehicle communication and vehicle-to-road communication, the amount of information collected and calculated by vehicles will further increase, and the requirements for the processing capability of vehicle-mounted terminals will become higher and higher.
The richness of functions leads to an increase in system complexity, including coordinated development in chips, sensors, mobile internet operating systems, communication devices, and communication services. The complexity of the overall network architecture has increased the exposure of vehicles to various attacks, and information security requirements have become more important and urgent. The confidentiality, integrity, availability, certifiability and auditability of the basic attributes of information security present different priorities in the specific application field of vehicle-mounted terminals.
The in-vehicle terminal's authentication requirements for access and use are particularly prominent – ​​it ensures that the information is used by the right person, and the correct user with the appropriate authority is given the order. In other words, whether a malicious attacker can damage the security protection of the vehicle terminal, and intentionally issue various instructions to the ECUs of the vehicle electrical and electronic system, threatening the safety of the normal user of the vehicle, and is an information security that must be considered when designing and implementing the vehicle terminal. main issue.
Integrity is also a relatively important aspect of information security attributes compared to certifiability. Once the transmitted information and instructions are tampered with, it can result in different or even the opposite operation of the authorized user's intention, resulting in information security and serious incidents involving personal safety.
Availability is also a security attribute that needs to be protected for driving applications that rely on vehicle terminals. Many attacks are often the first to attack availability when they are not familiar with the vulnerabilities of the vehicle system. After disrupting the normal operation of the system, look for security weaknesses and make deep breakthroughs.
Confidentiality is the basis of information security attributes. Most attacks usually start with sniffing and obtain the plaintext information or signals transmitted by the user, including the user name and password, to understand the application used by the user. Destruction of confidentiality not only violates privacy, but also facilitates other attacks.
Auditability is the foundation of information security work. Only information security incidents can be audited, and problems can be discovered and dealt with in a timely manner to avoid problems or more serious problems.
2. Classification of information security threats faced by vehicle terminals
2.1 Classification according to the destruction of the information security attributes of the vehicle terminal
As described above, the information security attributes of the in-vehicle terminal include confidentiality, integrity, availability, certifiability, and auditability. Some threats are aimed at the confidentiality of in-vehicle terminals, collecting user data, resulting in privacy leaks; some threats destroy integrity, and some even destroy information security attributes. This paper classifies threats according to the destruction of the information security attributes of the vehicle terminal, and introduces them in a targeted manner (see Table 1).
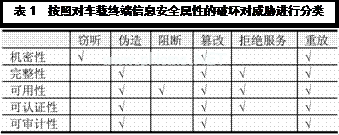
(1) Eavesdropping
The most basic threat is the basis of other attacks. The connection between the vehicle terminal and the cloud is used to transmit a large amount of user privacy data, such as driving data, vehicle status information, etc., which are sniffed in the network. For the in-vehicle network, when the vehicle terminal is connected to the car bus, the risk of the various control commands and system information transmitted on the CAN bus being attacked by the attacker increases. Once the attacker gains control of the in-vehicle intelligent terminal, it is easy to obtain the information transmitted on the connected bus.
(2) Forgery
Due to the lack of authentication of the data, an attacker can inject the virus-infected code or code that may cause a stack overflow, or an unauthorized command, to the vehicle-mounted terminal to perform any operation on the vehicle-mounted terminal operating system, the application, and the in-vehicle ECU.
(3) Blocking
The information and instructions sent by the cloud to the car may be interfered by the attacker at the network level, and may not reach the vehicle terminal normally. Once the vehicle terminal is illegally controlled, the attacker can block the information forwarded by the communication gateway of the CAN network, thereby implementing a blocking attack on the electronic and electrical system in the vehicle.
(4) Tampering
Tampering attacks combine a variety of methods such as eavesdropping, blocking, and forgery to form more complex attacks. The attack can tamper with relevant data such as driving directions received by the driver of the vehicle from the cloud, or may be status information returned from each ECU in the vehicle, affecting the normal judgment and operation of the driver; or an instruction to send the driver of the vehicle to the ECU. Make modifications to interfere with normal vehicle travel. The consequences are very serious.
(5) Refusal of service
Dustproof Miniature Micro Switch
Features
â—† Inner Housing tunnel design, silicone ring sealing design, stable
sealing IP60.
â—† Small Compact Size,Safety Approvals.
â—† Long life & high reliability.
â—† Wide Range of wires Terminals.
â—† Variety of Levers.
â—† Suit of harsh environment applications, Such as vacuum cle
Wireless Micro Switch,Micro Touch Switch,Ip60 Dustproof Switch,Dustproof Miniature Micro Switch
Ningbo Jialin Electronics Co.,Ltd , https://www.donghai-switch.com