Being able to witness the emergence of an industry, from cowardice to embarrassment, is a fortunate career. This may become a memorized sample worthy of collection.
Li Wei is such a mobile security veteran. In 1998, before the concept of mobile security was born, he was sitting in Motorola's office to develop the core components of the pager's system. Looking back now, China's mobile technology has exploded. It seems that the Tianshui pingchuanchuan is the “small black box†that starts from people's waists. In this way, he contacted the earliest mobile devices in China and the first batch of mobile communication users who had reached the age of destiny.

Li Wei
In Li Wei's eyes, this nearly 20-year history is closely linked to his most prosperous years. There is a different kind of warmth.
Motorola, Saipan, a pioneering era of mobile securityLi Wei, who spent three years developing Windows applications after graduating from college, feels that the Windows system has become increasingly large and even somewhat formulaic. At this time, the unique technical beauty of the embedded system attracted him. Occasionally, he saw the mobile pager business of Motorola being recruited and began his career in mobile devices.
At that time, a better pager required more than 2000 yuan, which was very expensive. But the drawers of every person in our office are pulled open, full of pagers.
Li Wei recalled with great interest.

Motorola pager
The system of a pager is simple, but it has a wealth of technical details. Li Wei gave an example to Lei Fengwang. The base station of the paging station broadcasts signals in the form of broadcast. All pagers can receive it, but only one pager must be able to interpret this signal. This involves the technology of number identification and paging protocol that he is involved in research and development.
However, as the turn of the century approached, the pager, which temporarily occupied people's lives, was quickly pulled down by the mobile phone. Li Wei also naturally became China's first batch of mobile phone development experts. Even if speaking from the interface and ease of use, the mobile phone at that time can be described as simple. But even so, safety technology is essential.
Under the circumstances at the time, there were no loopholes and security concepts that used loopholes to raise power. Because the mobile phone system is a special resource, it is necessary to design the mobile phone completely different from the PC's set of rights access modes to restrict the access of malicious resources. For example, "drm" is a system that limits the number of accesses and forwarding of resources. Moreover, at the time, we also designed a hardware layer, a driver layer, and an application layer protection system to prevent possible loopholes at any level.
Li Wei told Lei Feng Network that this was his earliest involved security project.
However, he felt vaguely uneasy, because in his imagination, a mobile phone should carry a complicated operating system. This idea eventually prompted him to join Sybian, who later became famous in 2005.

Saipan was not yet acquired by Nokia. As the first engineer of this smart system in China, he was responsible for Saipan's technical guidance and docking for developers throughout the Chinese market.
Because I have a lot of mobile device embedded development experience, I am very familiar with the underlying logic of mobile systems. The closer to the bottom of the system, the higher the logic similarity of each system. At the kernel level, the logic of Symbian, Android, and iOS are all very similar. The applications related to the underlying system only have one security category.
Li Wei explained why he embarked on the safe road to move. It is also at this time that the security of mobile systems really begins to surface.
At the time, the mobile phone virus was a rare species, but it has become a problem that cannot be ignored for mobile phone system vendors and software developers. The teams who developed anti-virus software have also become frequent visitors to Li Wei’s office. For example, Netqin, who became famous at a later date, for example, a cell phone anti-virus software called "Xin Anyi," later became a 360 mobile phone guard.
The first batch of Root Android in ChinaIn 2010, the 3Q war broke out. It now appears that this classic war in business history has become the first year of China’s mobile security technology arms race. That year, with Motorola and Saipan systems as the two biggest auras of mobile communications history, Li Wei has become China's few hot mobile phone security experts at the time.
Tencent, who is preparing for full firepower, extended an olive branch to him and Li Wei set up a mobile safety laboratory.
“The bottom-down confrontation of Andrews is simply the ability to inject and counter-inject. At that time, Tencent’s ability in this area is relatively weak. I can say that it is a threatened task.†Li Wei recalled. In fact, when we look back at the cell phones in 2016, Android is only one year old. According to Li Wei, not only Tencent, but everyone's Android security framework “is in an awkward stateâ€.
The world's first Android phone HTC G1
In order to fight viruses and malware, Li Wei must find a technology that keeps the kernel layer from the application layer to get the system's underlying permissions. The core technology of this is Root, which we now know well. Only at that time, the word had not yet been invented.
In early 2011, Li Wei judged from experience that this kind of technology that could “break the system structure†existed. Moreover, another thing corroborated his judgment.
Zhang Yong of LBE is my friend. He is the first person to make an Android Root in China. Since he has done it, I believe it can definitely be done.
In June of that year, Li Wei started research on "low-level privilege control technology" with two brothers. The difficulty of this technology lies in not only requiring researchers to master the underlying logic of Android, but also to have a deep understanding of the upper service layer and framework layer. For Li Wei, he still needs to complement the upper layers of the Android system from scratch. During that time, working two or three nights a day was his normal.
Although the root technology for the Android system is now available, open source technologies and architectures can be found on the Internet. But it was still very difficult to get Root out of it without any reference.
Li Wei said.
Two months later, the laboratory successfully delivered this "bottom access control technology" to Tencent. He is not without pride to recall that this technology "leads the opponent six months."
The Chinese leader of the first batch of Root Android systems did not recall too much about the difficulties. However, from the beginning to build the root world view from scratch, one can imagine what kind of "power of the prehistoric" he has produced.
Virus WarAfter completing the development of Root technology, the Mobile Security Lab has received a new task, which is to improve the mobile phone housekeeper's ability to kill mobile phone viruses.
"Android is a new platform. At that time, malicious software broke out. All the industry's killing rates are not good. The industry urgently needs a system with virus capture capability," he said.
The virus is often hidden in the App for propagation. The industry generally believes that an automatic analysis and processing system for the App is the best solution. However, Li Wei was not satisfied with the analysis system framework adopted by Tencent at that time. He decided to implement some improvements to improve the accuracy of virus identification.
The difficulty in identifying a virus is that you must know what malicious behavior an app actually has.
For example, reading a phone book, uploading information. The two actions themselves are fine, but if a program first reads your phone book and then uploads it to the server, this action is suspicious.
However, the difficulty is also here. It is very simple to judge the program to read the phone book and upload data. However, it is very difficult to identify the logical relationship between the two actions. It is necessary to analyze the execution flow of the program, or to require virtual execution. .
Li Wei designed the system to simply screen a large number of apps with as many behavioral models as possible. In 2011, the system will screen tens of thousands of documents a day. In order to ensure accuracy and improve the system, there will be a large number of manual retests. "Perhaps each person audits the codes of hundreds of apps every day," recalls Li Wei.
Li Wei is pleased that these hardships have not been paid in vain. After one year of optimization, Tencent’s cell phone virus detection capability has finally reached the leading domestic level in 2012, and scored a perfect score in an international assessment.
In addition, Li Wei has been dissatisfied with the design of the initial anti-virus engine. In his words, the design is "a bit rough."
For example, the installation package of a game may reach 80M. The anti-virus engine on the mobile phone will put all of the 80M files in the memory, and then detect it. This method of processing consumes a lot of memory and takes a long time to detect.
We designed a method to apply a small piece of memory to the system for virus scanning. In an 80M APK installation package, it is very likely that the real code is only 4M. The rest is resources and pictures. In this case, it is only necessary to put the code portion that may contain malicious programs into the memory to detect and fully implement the virus killing.
This principle sounds very simple, and it is not complicated for the technical level of the laboratory. Facts have proved that they use this technology to achieve a tenfold increase in the speed of antivirus. The team found that the technology they invented was already at the forefront of virus killing, so it also applied for a patent. "This leads to competitors must adopt other technical routes." Li Wei said.
Late night chaseAlthough China's mobile anti-virus software technology is advancing at a rapid rate, the strong momentum of malicious software has not diminished. Li Wei told Lei Fengwang (search "Lei Feng Net" public number attention) about the most exotic and most unforgiving malware he encountered in 2012.
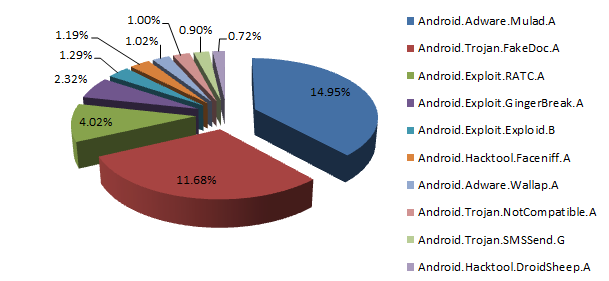
2012 Android System Malware Classification
The virus detection system caught a malicious program and we manually screened it. We have discovered that this virus will cover a layer of windows above popular programs such as WeChat, maliciously promoting its advertisements, and inducing users to download other apps. The awful thing is that it also has some interactive buttons that give the user the feeling that WeChat is pushing these ads. Even more abominable is that it will change the style of the button according to the invading app, so that the user feels seamless.
Li Wei, who has done anti-virus work for many years, feels unbearable, and hackers actually lie on the door of their own WeChat "failure." Even more frightening is that by using Android's system privileges, this virus can get a lot of users' private information.
Li Weihe team analyzed the malware code and found out the server address it used to control and connect back. After a public data query, it is easy to locate the real name and address of the virus author. After communicating with the upper level, Tencent decided to call the police.
From the discovery of the virus, to the analysis and research, the positioning of criminals, to the reporting of the police, all things happen within one day. I remember that late at night, the public security team needed people to go to Jiangsu to cope with the case overnight. Many of our team members did not bring their ID cards. Fortunately, colleagues with ID cards did not have time to go home and bought tickets directly to Jiangsu. The criminals were brought to justice on that day.
Now think of this "late night chase" story, Li Wei still can not conceal the inner waves. For most viruses, antivirus software can only intercept and kill, but there are not many actions like this time. For him, doing cell phone security for more than a decade, the scene before him convinced him of the value of his work.
Defend the AppIn 2013, Li Wei noticed a special trend, that is, many viruses no longer focused on the Android system, but directly "applying the App." With this idea in mind, Li Wei started to develop a system to monitor the loopholes in the App, and instinctively tested its apps such as WeChat. This investigation does not matter, he did find that there are many problems with their own products, which makes the team scared of a cold sweat, urgently repaired the core products such as WeChat.
So Li Wei noticed that "application security" is very likely to be a very important security direction in the future. So he put the focus of the mobile security laboratory on the "application hole" research.
Compared to attacking Android systems, the cost of attacking an app is low. And the App and the user have recently had a lot of personal information. These are the black production's most concerned. Obtaining a personal address book or relationship chain through an intruder app is much simpler than invading the system.
Li Wei said.
The most common vulnerabilities for an app are the following:
1. Many applications will use the Webview embedded browser. If the security mechanism is not done enough, it may become an attack entry. When a user opens a malicious url through Webview, a remote attack code is executed.
2. Some apps may also be networked through their own protocols. In this case, hackers can send malicious code to the client through a "man in the middle" or "forged server" method.
3, there is a mutual call mechanism between the App in the Android system. If the call interface security is not high, App 1 can use App2 to execute some malicious code to steal privacy information from the App.
In plain terms, if a chat app is attacked, it is very likely that the victim has scanned his QR code and stole his address book and relationship chain. If the vulnerability is serious (such a loophole is also repeatedly discovered), It is possible to cross App attacks.
He told Lei Fengwang that, to some extent, finding an application's vulnerability is more difficult than finding an operating system's vulnerability because the attack requires entry, and the open interface of the application is far less than the interface open to the operating system. He said:
App exploits and system exploits are different.
The user of the system is the App, and the App may call all system interfaces.
The user of the App is a person. People generally use only a limited number of interfaces, such as: network access, voice, scan code, and information typing.
So we can only do articles through these interfaces.
Li Wei's App vulnerability mining ideas, to some extent, and Tencent's another big cattle, Wu Shi, who studies system loopholes are somewhat similar. (For the study of Wu Shi, please punctuate Lei Feng: "Cohen's laboratory Wu Shi: People standing between 0 and 1")
This method of inputting specific data is essentially a virtual execution. We must enter specific data from these interfaces, causing the App to run in error and thus discover and exploit vulnerabilities.
Data input actions are largely automated. Based on our experience, we discovered weaknesses in the App and then used automated tools to generate some extreme data to observe the different responses of the App.
Invisible opponentApp vulnerability research is a chore because App is not standardized in most cases. For researchers, although experience can be reused, research must be conducted separately for different apps. Moreover, since App security is limited by the country and user groups, there is no system vulnerability. However, Li Wei feels that the work of the mobile security laboratory is of great significance.
We will study the top 200 on the market and the larger number of users. From 13 years to today, a total of more than 100 high-risk vulnerabilities have been discovered. These vulnerabilities cover 1 billion users.
In theory, exploits for apps are hidden. If black production has already stolen the user data of some apps, it will only generate traffic at the time of stealing and will not leave evidence such as data packets. Li Wei told Lei Fengwang that it was difficult to generate official statistics on whether the user information of an app was stolen in the industry. Therefore, Li Wei and his team’s opponents are actually “invisibleâ€. All of their efforts are based on imaginary enemies and are sealed before the opponents discover and exploit the loopholes. If you attack a user with each high-risk vulnerability, they have blocked a potential 100 billion attacks.
Although opponents never showed up, Li Wei did not dare to slouch. In a sense, he is more like a star, but the Huns are seven hundred miles, building the Great Wall and keeping fences.
It is precisely because this battlefield is garrisoned by many hundred famous players like Li Wei. Only then can the virtual world between the squares run as usual.