The types of attacks on smart meters can be roughly divided into physical attacks (external interference, bypassing the neutral line, missing neutral line, etc.), electrical attacks (over / undervoltage, circuit detection, ESD, etc.) and software and data attacks (spyware insertion, network attack). In addition to physical tampering with the meter, most of the known vulnerabilities are related to communication media and communication protocols because the grid is already interconnected.
Solutions for physical tampering include the use of magnetic sensors (detecting whether there is a strong magnetic field, which can affect the current transformer meter reading), tilt sensors, which can detect whether the meter at the authorized location has been removed or physical tampering, and use tampering in firmware The algorithm helps to ensure continuous billing. A tamper-proof switch can also be placed on the meter casing. When the casing is opened, a tamper notification can be triggered.
Automatic metering systems include software, hardware, communications, customer-related systems, and meter data management (MDM) software. As the meter becomes intelligent and networked, the meter software must provide sufficient security features to prevent illegal changes to the software configuration, readings of recorded data, and modification of calibration data. The solution needs to incorporate security technology to ensure the security of the communication channel and the physical security of the assets, making the smart grid more secure and reliable.
Secure communication protocol
Currently, there are various data exchange protocols used by parties in the power grid. Transmission control protocol (TCP) / Internet protocol (IP), hypertext transfer protocol (HTTP) and file transfer protocol (FTP) are widely used in the global information technology field. Because the transmitted data is easily stolen by hackers, the data is not very secure and vulnerable to attacks. For power grids or smart meters, non-secure protocols must be replaced with protocols such as Internet Protocol Security (IPSec), Secure Sockets Layer (SSL), Transport Layer Security (TLS), and Secure Shell (SSH). IPSec uses encryption technology to ensure the data confidentiality, integrity and authenticity of the communication parties between private networks.
High-level security for control and command
Symmetric key cryptosystems such as AES are suitable for batch data, but the security level is not high. Asymmetric key cryptosystems such as the Elliptic Curve Digital Signature Algorithm (ECDSA) are suitable for encrypting remote disconnect / connect real-time electricity price changes and other control / commands. This ensures that the commands to control the grid equipment are highly authentic. Key exchange based on elliptic curve encryption (ECC) provides a high level of security. Wireless networks such as Zigbee® can use ECC to provide digital certificates to exchange information between ZigBee nodes / devices in the smart grid ecosystem.
Encryption Technology
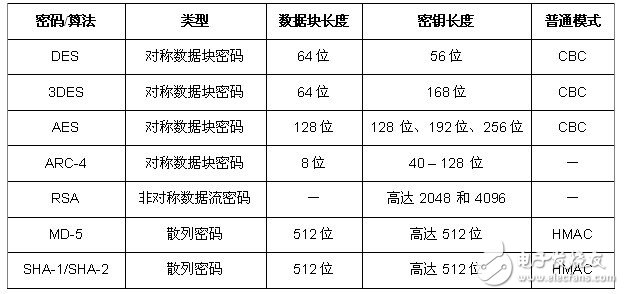
Note: Almost all security protocols require one or more encryption technologies to encrypt data. The 128-bit AES password is widely used in smart meter applications and for communication between a single meter and the meter data collection device. Since the data is encrypted, it can be prevented from being stolen.
Key generation and storage of encryption algorithms
Almost all security passwords and password keys rely on random seeding. Using a pseudo-random number to generate the key will result in pseudo security. The National Institute of Standards and Technology (NIST) uses a file transfer protocol 140-2 compliant random number generator to ensure high security. It is recommended to use hardware instead of software to generate random numbers and delete the key when a cracking event occurs.
Cassava Dregs Separator,Cassava Processing Machine,Cassava Processing Equipment,Cassava Milling Machine
Hunan Furui Mechanical and Electrical Equipment Manufacturing Co., Ltd. , https://www.thresher.nl