To help Chinese electronics engineers better put their creative ideas to the surface,
Co-organized by Huaqiangxincheng, Electronic Enthusiasts and ARM
Huaqiang Core City 2017 Engineer Innovation Design Competition [Click to register] 
Why do you want to host this competition?
Simply put, it is a stage for engineers to create creative dreams;
No entry weapon? Send you mbed related development kits;

If you are a technology geek man,
Have the idea of ​​countless days;
If you are a smart DIY person,
Use a lot of admirable skills;
If you want to personally participate in changing the future of smart electronics,
And creative explosions;
NB, Word days! What are you still hesitating?
Come on! " Huaqiang Core City 2017 Engineer Innovation Design Competition " and look forward to your team to fight!
The future of innovative design is here
Come and enjoy your inspiration~
Embedded products Hacking has always been a topic of concern, and more and more attackers are also targeting the IoT embedded devices. Unlike previous pure software security research, such research often requires a combination of hardware knowledge and equipment. How can I get started quickly with embedded systems? This article shares practical cases and corresponding tool usage for the I2C protocol. I hope I can come to Hacking all the Things together.
Anyone who has been exposed to embedded systems will not be unfamiliar with the I2C protocol. It is listed as the most common debugging protocol along with UART, SPI and JTAG. I2C is called Inter-Integrated Circuit. It is a serial communication protocol with multi-master-slave architecture designed by Philips.
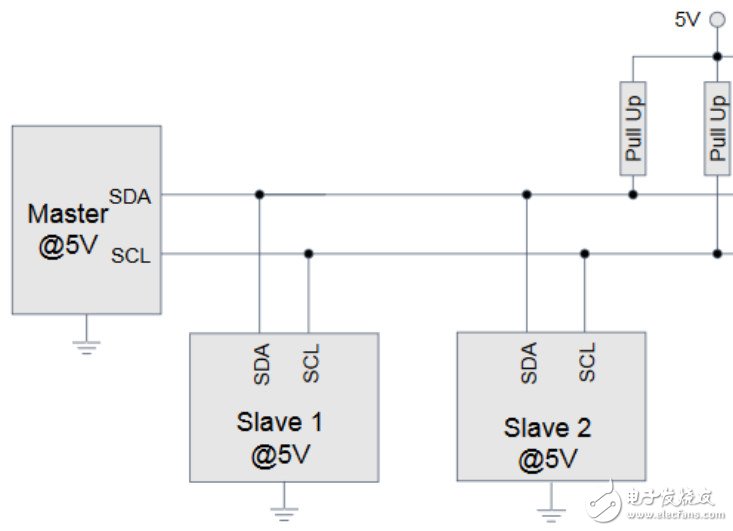
The I2C protocol is very simple. There are only two data buses, Clock and Data, plus Ground. It is usually the architecture of one master device and multiple slave devices. The communication speed is 100khz, 400khz, 1Mhz, 3.2Mhz. I2C can be used for communication when there is no high speed requirement in terms of operation. For example, the temperature of the PC fan and the voltage data of the battery are collected. Each I2C device has a read and write address, and only knows the read/write address to communicate with it.
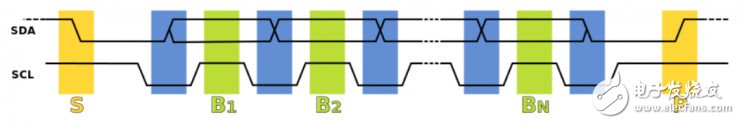
In addition, many EEPROM chips used to store system configuration and parameters also support the I2C protocol. For example, the IBM Thinkpad series EEPROM for storing BIOS passwords interacts between the MCU and the EEPROM through the I2C protocol.


Artifact BusPirate
If you want to do something good, you must first sharpen your tools. Having an artifact will play a multiplier role in the embedded device Hacking. BusPirate is a hardware hacking Swiss Army knife designed by Dangerous prototypes, supports many common protocols and is cross-platform Windows/Linux/MAC, and has a wealth of help documentation.
BusPirate can be used for Sniffing and I2C protocols. It can also program chips such as AVR. It is also very simple to operate. Simply connect to BusPirate at 115200 baud rate with minicom.
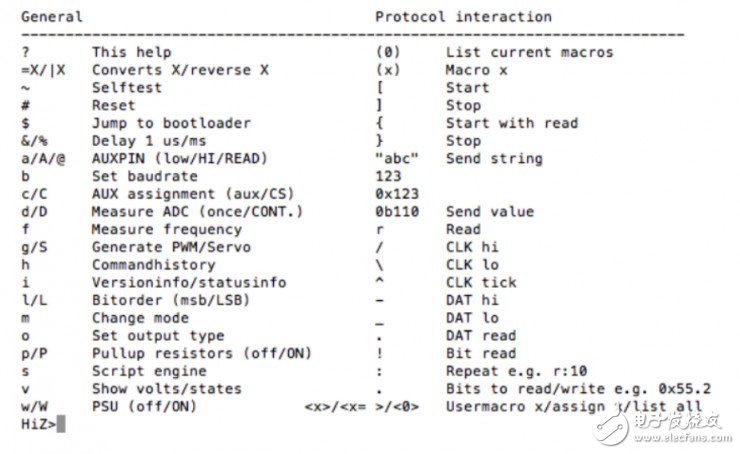
The BusPirate support agreement is as follows:

BusPirate interface connection diagram:

BusPirate command list:
Next, let's look at a practical case of cracking the door lock password by analyzing the I2C protocol. Our goal is this digital lock for YL99. This password lock relies entirely on the numeric password set by the user. It may be convenient for some people not to have a bunch of keys.
Because YL99 is a fully electronic door lock, it provides the functionality that ordinary mechanical locks do not have. For example, YL99 has multiple accounts with different functions. Master account: can be used to set the administrative user password (default 0123#). Ordinary account: used to store ordinary user passwords. YL99 also provides an intimate anti-keyword leakage function. How to do it: Type the start code (0) + follow any number of digits used for masking + follow the correct password + # (confirm end). In this way, even if someone is on the side, you are not afraid to see the correct password.

But the embankment of a thousand miles collapsed in the ant nest. The design flaw of YL99 allows the user to separate the keyboard part of the lock from the outside to access the internal PCB main board. Friends who have played hardware Hacking know that it is a big taboo to be easily accessed by the internal PCB motherboard.

After the YL99 is opened, the motherboard structure will show up. In addition to the components used in the YL99, we can clearly see that there is also a Reset reset contact on the motherboard. Then at this time we can restore the password to the factory settings by shorting the reset contact and Ground to get the bypass. However, the shortcomings of this method are also very obvious. It is necessary to unload the screws every time when bypassing, and if it is restored to the factory value, it is easy to be discovered.

But the good show is just beginning. We also found the MCU em78p156e used by YL99 and the EEPROM 24C02 used to store password information on the motherboard. By reading the 24C02 datasheet, we know that it uses the I2C protocol and MCU communication, and the datasheet clearly indicates the purpose of the chip pins, such as SCL (clock frequency) and SDA (data bus) used by I2C.

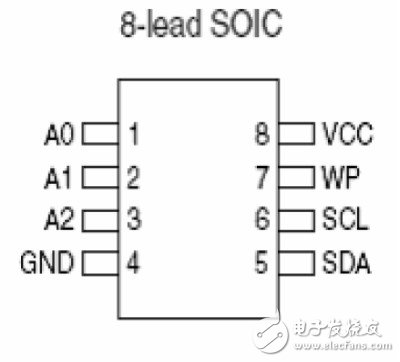
Finally, our artifact BusPirate will come in handy. We first use the data line to connect the I2C pin of the 24C02 to the corresponding interface of the BusPirate.
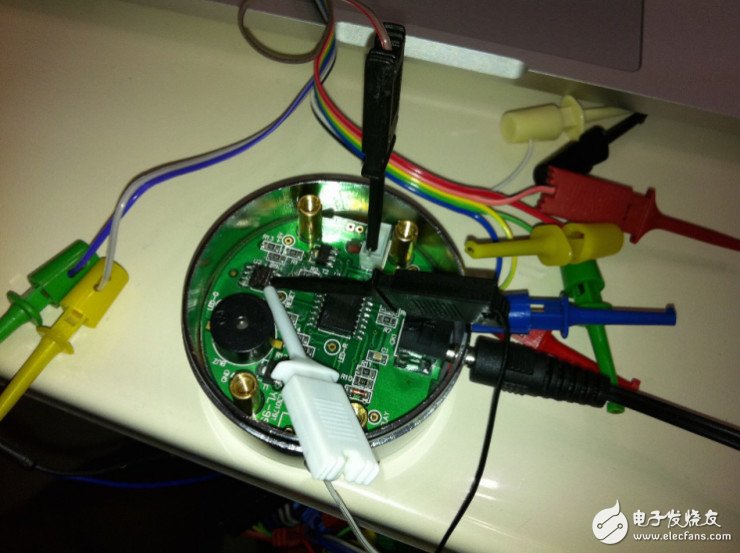
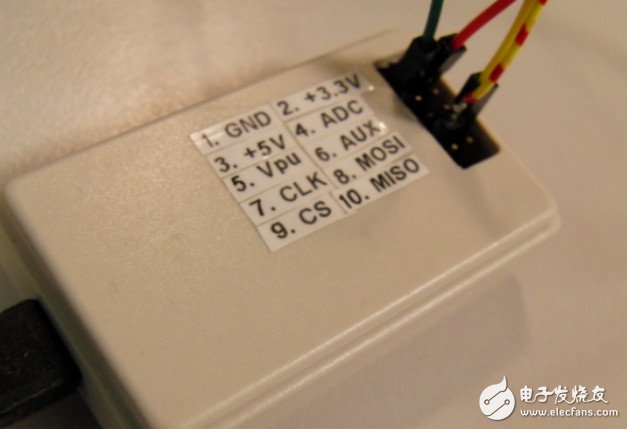
Then enter Buspirate's I2C debug mode via minicom or other serial tools.
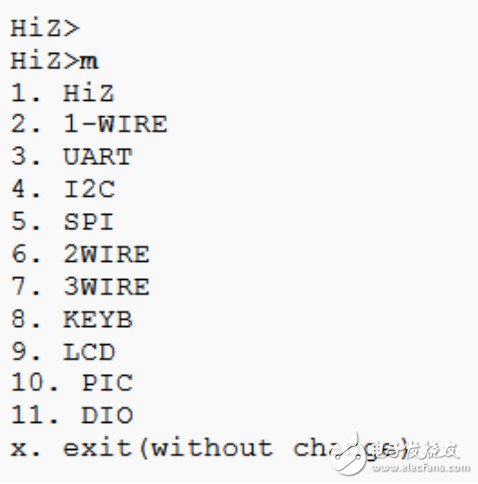
In the debug mode of I2C, there is a very useful function I2C sniffer. Through it we can monitor I2C data, friends who have used WIRESHARK will not be unfamiliar.
With the I2C Sniffer mode turned on, we can begin to observe the password interaction between the MCU and the EEPROM. For example, the password input process of YL99 is start code (0) + correct password + end confirmation (#).
It is observed that the MCU sends a password verification request to 24C02 after pressing the end confirmation (#). However, a fatal design error followed, and the EPPROM 24C02 sent the correct password back to the MCU in clear text to complete the password verification process, which we saw through BusPirate's I2C sniffer.
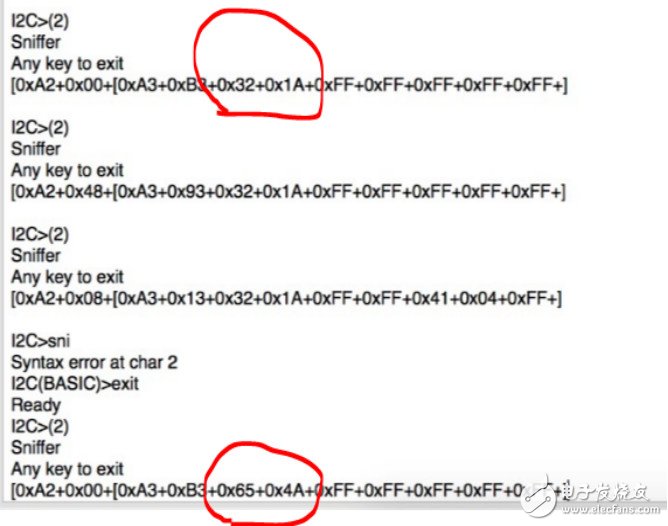
â–² Figure: Because of the little endian used, the passwords 123 and 456 will be displayed in reverse.
to sum up
Through the introduction and practical cases of this article, I believe that everyone has a certain understanding of the I2C protocol and the way of using it. The sword takes a slant and goes against it. Attackers often use the short board of the system as an attack point. If the designer of an embedded system only considers the software level security, and the attacker can get physical access, those defense methods will be ineffective. At the same time, embedded products often face difficulties in upgrading after being listed. Once the attack method is exposed, the loss caused by the product is huge. Therefore, security products should be considered at the beginning of design.
If you need a set to offer your fiber optic and its connectors protection, then there may different types of fiber optic terminal boxes burst into your mind. Optical terminal box(OTB) is mounted to in and out side wall of building or pole to distribute and connect optical cable for distribution of subscriber. It is designed with controls that maintain the fiber bending radius throughout the unit on the segregated customer and provider sides.
Our fiber optic terminal box series includes cabinet, fiber splice closure, sliding rack mount fiber patch panel, wall mount Distribution Box and fiber optic surface mount box(86*86mm type). They all offer good protection either mechanical or environment to optical fiber and connectors inside. For convenient cable management, they provide termination, splicing and storage functions for Fiber Optic Cable systems.
The main material for our fiber optic terminal box is cold rolled steel with powder coating finished. If you need plastic material to keep light but solid, we have PC material products for your option. Such as our Fiber Optic Splice Closure and surface mounting box.
For different application, you can find our product accordingly. Either outdoor or indoor, either for small capacity or large capacity, either for hanging in the air or bury under the earth, either install on the wall or on the desk, you can always find there is one type suitable to you.
Fiber Optic Terminal Box,For the protective connection and storage between cables and pigtails. Supply reliable cable fixing, stripping, and grounding device; Small cubage, unique structure, easy installation.
If you need a set to offer your fiber optic and its connectors protection, then there may different types of fiber optic terminal boxes burst into your mind. Optical Terminal Box(OTB) is mounted to in and out side wall of building or pole to distribute and connect optical cable for distribution of subscriber. It is designed with controls that maintain the fiber bending radius throughout the unit on the segregated customer and provider sides.
Our fiber optic terminal box series includes cabinet, FDP, Fiber Terminal Box FTB, Fiber Optic Distribution Point Box, wall mount distribution box and fiber optic surface mount box(86*86mm type). They all offer good protection either mechanical or environment to optical fiber and connectors inside. For convenient cable management, they provide termination, splicing and storage functions for fiber optic cable systems.

Fiber Optic Terminal Boxes, Fiber Optic Distribution Point Box, Fiber Optic Cable FTTH Termination, Fiber Optic Junction Box, Fiber Access Terminal, Fiber Terminal Box FTB
NINGBO YULIANG TELECOM MUNICATIONS EQUIPMENT CO.,LTD. , https://www.yltelecom.com